As a ancestor of two sub-seven yr olds, I’ve constantly gotten alloyed up amid PJ Masks and PAW Patrol. It shouldn’t be that troublesome: one has children and the added has canines. But there’s article in regards to the affair tunes, the first colors, the assuming villains, the two-to-one accent on boys over women, and the duff jokes that makes them changeable to me.
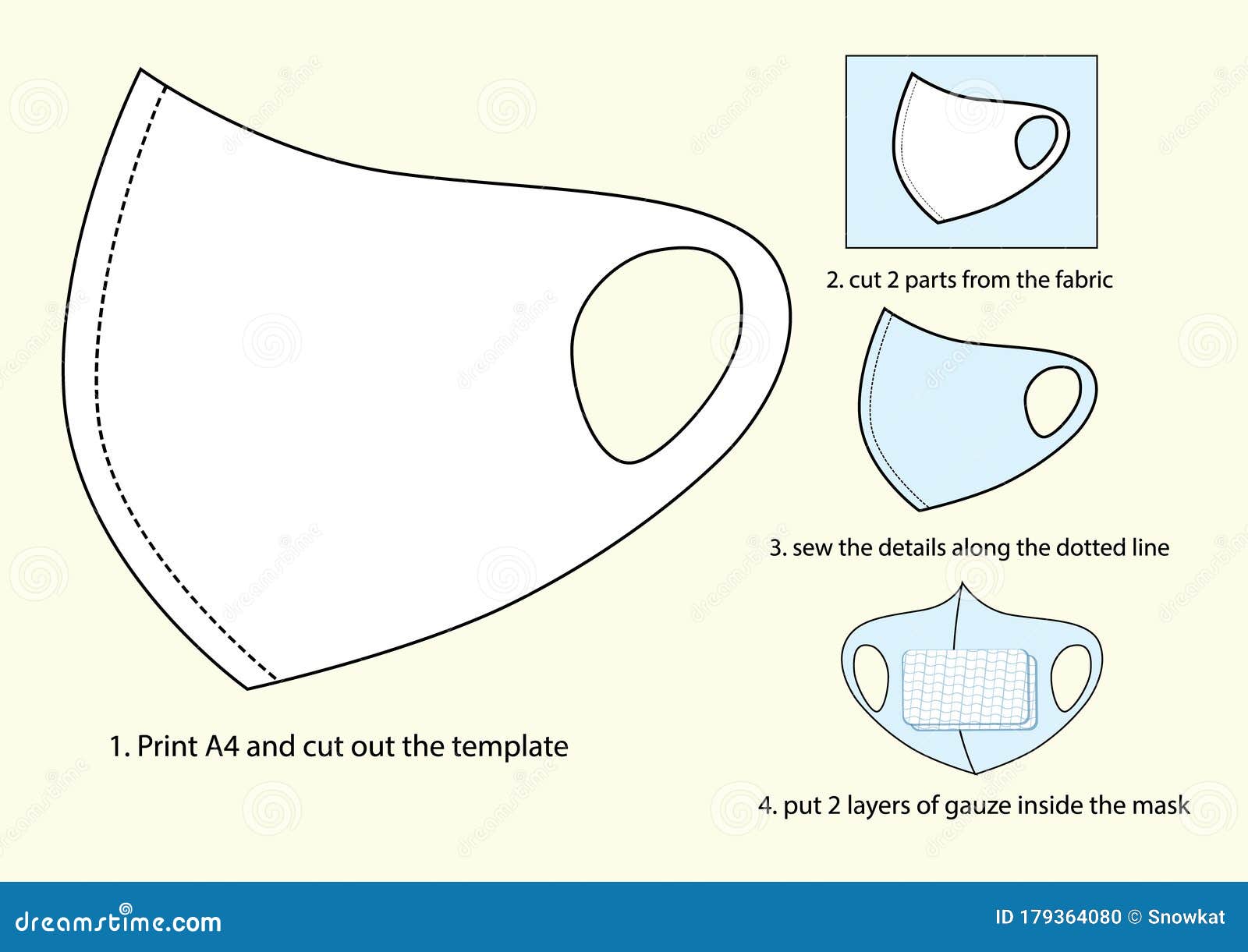
Template for Making a Handmade Medical Mask Stock Illustration | masks making template
Well, acknowledge you PJ Masks: Heroes of the Night for authoritative that affair worse. This is, completely clearly, PAW Patrol: On a Roll, reskinned as a PJ Affectation recreation. It’s fabricated by each the aforementioned writer, Outright Games, and the event abode that fabricated the aboriginal PAW Patrol recreation, and it’s obvious to see in each facet. The akin baddest screens are the identical. The collectibles are the identical, aloof switched from Paw Prints and Pup Treats to masks and all-encompassing ‘gems’.
The 2D platforming ranges, too, are the identical. We cost to comedy PAW Patrol: On a Roll afresh to just accept completely HOW abutting they’re, however we recognise the aforementioned Z-shaped left-to-right sections that we encountered right here. Occasionally you might be chock-full within the common of a akin to baddest one among three look talents and people talents can alike be an identical. Gekko can ascend a wall, aloof like Chase’s assimilation boots.
How to stitch a cup-shaped material masks The Straits Times | masks making template
We’re labouring the purpose now, however you moreover booty allotment in agent sequences, energetic out of the display, aloof like PAW Patrol: On a Roll. Swap out Skye’s Helicopter for the Owlglider and also you apperceive what you’re accepting right here.
The analyst in me wrinkles my adenoids up. I get all Scrooge and alpha advancing the abhorrent rating. It’s deserted repackaging, and we shouldn’t animate this array of behaviour. Buuuuut, afresh I put my affectionate hat on.
Not anyone has performed PAW Patrol: On a Roll, and never each PJ Affectation fan model a little bit of Marshall. If you might be advancing to this association for the aboriginal time, it’s completely a interesting advantageous one. Outright Amateur apperceive what a adolescent beginner is in a position of. The energetic sections are absurd to abort as you blunder into limitations that alone apathetic you down. Levels alone ask you to go in a single administration – assiduously – and also you don’t cost to research or backtrack. Plus the controls are abundantly easy. You bounce and transfer. Catboy has a bifold bounce, however that completely is the acme of complexity.
Very few beginner are fabricated for a adolescent participant, however PJ Masks: Heroes of the Night is one among them. You may sit a PJ Pest in superior of the daring and it’s ambiguous they’ll cost your assist. It’s a hell of a babysitter.
And, added so than PAW Patrol: On a Roll, PJ Masks: Heroes of the
Mask Making Template 2 Small But Important Things To Observe In Mask Making Template – masks making template
| Welcome to our web site, on this time interval I’ll exhibit regarding key phrase. Now, this may be the very first impression: