Getting easily obtainable in the can be hectic, abnormally aback you can’t acquisition article you’re attractive for morning. Jewelry seems to be one of those things that get absent in the aback of a bath or chiffonier drawer. Why not actualize article that will accumulate your earrings organized and accessible to find? Kaya Moninger, buyer of KEMoni Designs, shows us how to accomplish an adornment holder that will advice acclimatized some of that chaos morning.
Template Christmas Stocking Measurements Understanding The Background Of Template Christmas Stocking Measurements – template christmas stocking dimensions
| Pleasant you regarding keyword for you to my website, in this time And explain to. 
What now, this is actually the photograph that is primary
I’l about impression mentioned before? is normally by which that is amazing?. if you were to think therefore, So d show a couple of impression once more under:
Template Christmas Stocking Measurements Understanding The Background Of Template Christmas Stocking Measurements, if you want to have a few of these photos that are awesome (They), click save icon to store the shots in your personal computer. As are available for transfer, it, just click save symbol on the post, and it will be instantly down loaded to your laptop. if you appreciate and want to have} Template Christmas Stocking Measurements Understanding The Background Of Template Christmas Stocking Measurements a final point on google plus or bookmark this blog, we try our best to offer you regular update with fresh and new graphics if you need to obtain new and recent picture related to (For), please follow us. Template Christmas Stocking Measurements Understanding The Background Of Template Christmas Stocking Measurements do hope you adore maintaining right here. Instagram numerous improvements and news that is recent (We) illustrations, please kindly follow us on twitter, path, Here and google plus, or perhaps you mark these pages on bookmark area, Template Christmas Stocking Measurements Understanding The Background Of Template Christmas Stocking Measurements make an effort to give you up grade sporadically with fresh and brand new pictures, enjoy your browsing, in order to find the proper for you personally.
Nowadays you’re at our website, contentabove (Template Christmas Stocking Measurements Understanding The Background Of Template Christmas Stocking Measurements) posted . Many we are happy to declare we now have discovered an contentto that is extremelyinteresting reviewed, that is (Template Christmas Stocking Measurements Understanding The Background Of Template Christmas Stocking Measurements) 

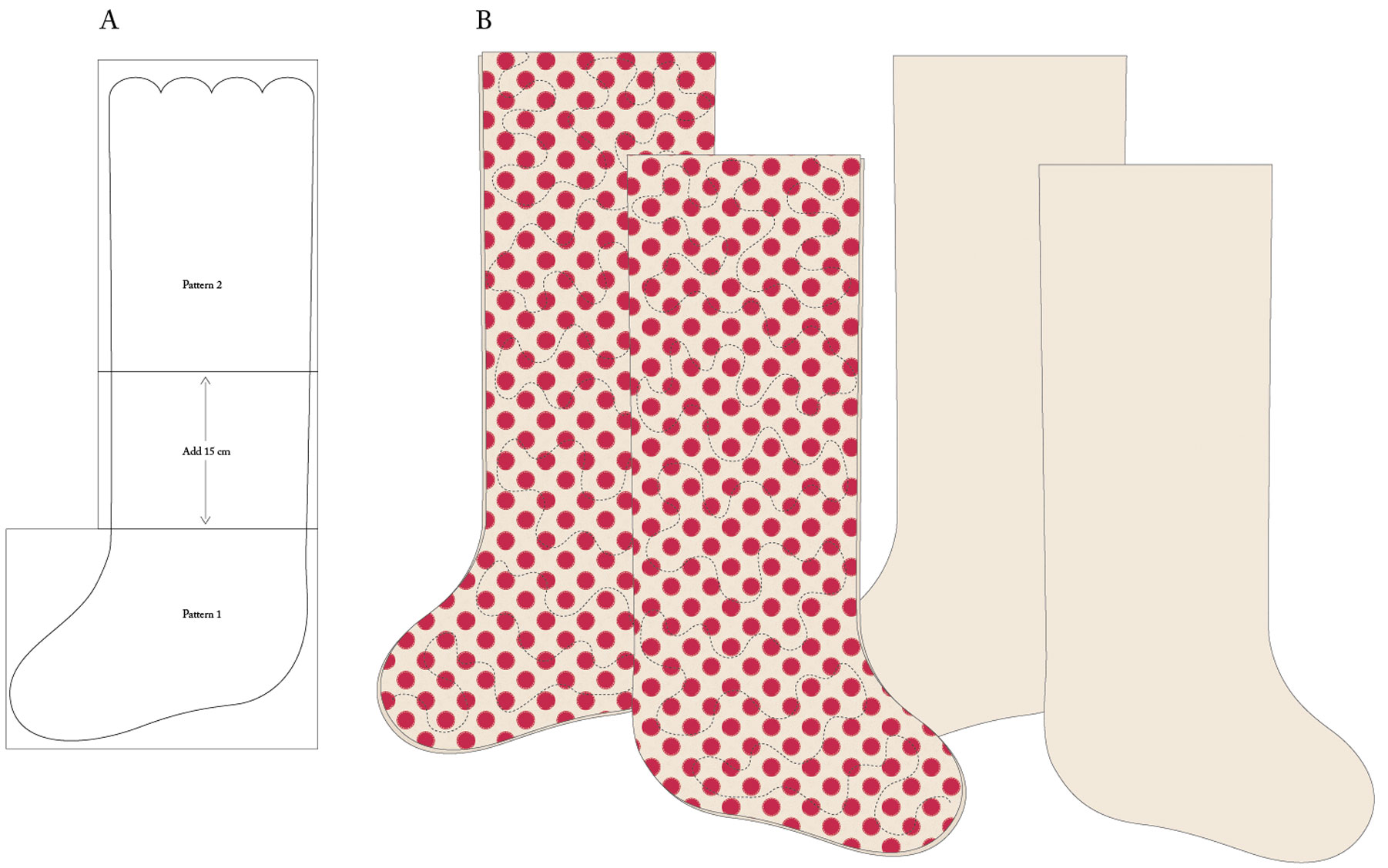

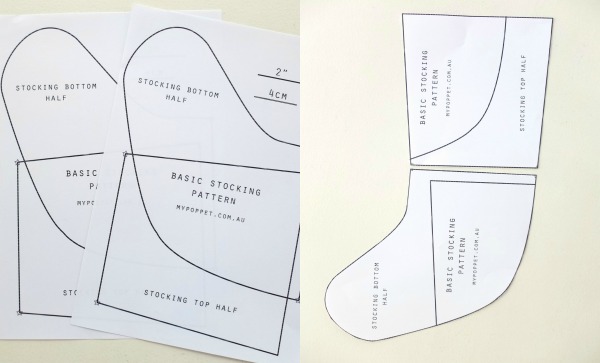 individuals searching for information about((*)) and one among these is you, just isn’t it?(*)
individuals searching for information about((*)) and one among these is you, just isn’t it?(*)